Questions this page should answer
- Who currently has access to this organization?
- How do I invite a new member with the right scope?
- How do
None,View only, andFullactually affect access?
Before you use this page
- In the app, open Organization settings and select
Members. - Confirm you have members write access.
- Check seat availability before bulk invites.
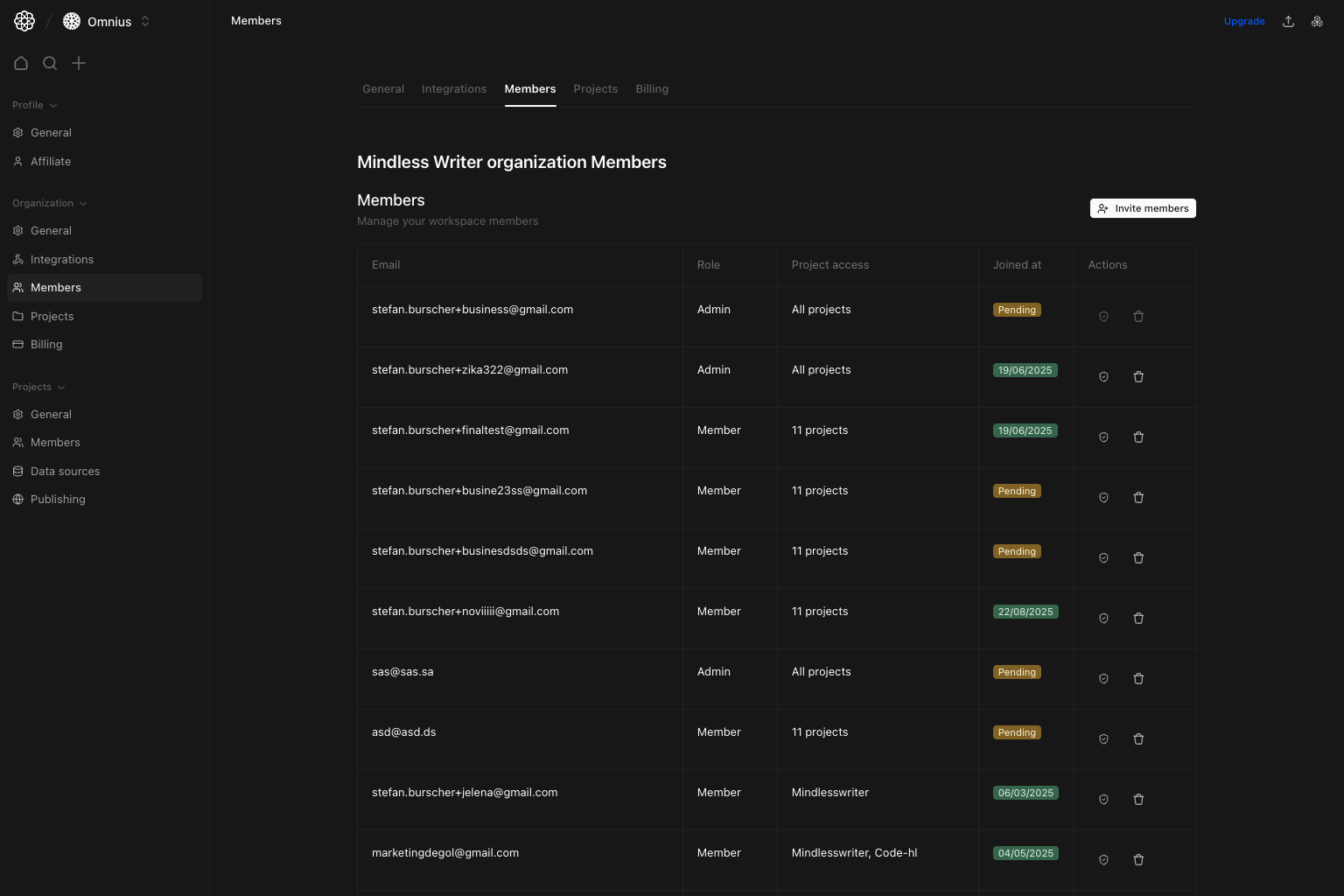
What this page controls
- Member directory (
Email,Role,Project access,Joined at,Actions). - Invite flow with role + workspace permissions + project permissions.
- Edit permissions flow for existing members.
- Member removal.
Invite members flow
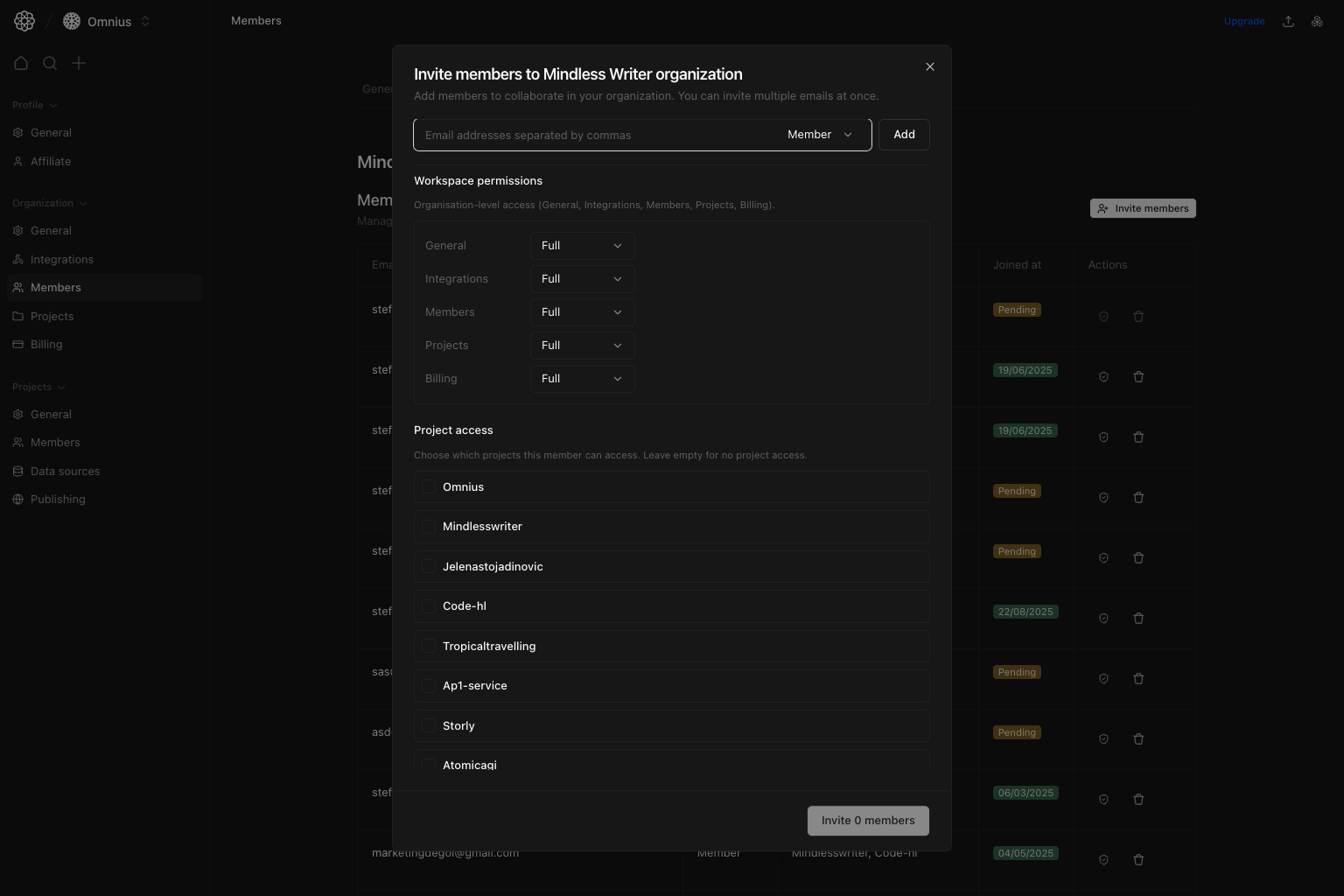
Invite members opens a dialog where you define access before sending invites.
How to invite correctly
- Add one or multiple emails.
- Select role:
Admin: full access across workspace and projects.Member: granular permissions are applied. - Set
Workspace permissions(General,Integrations,Members,Projects,Billing). - Select project access.
- For each selected project, set feature/settings permissions.
Edit permissions flow
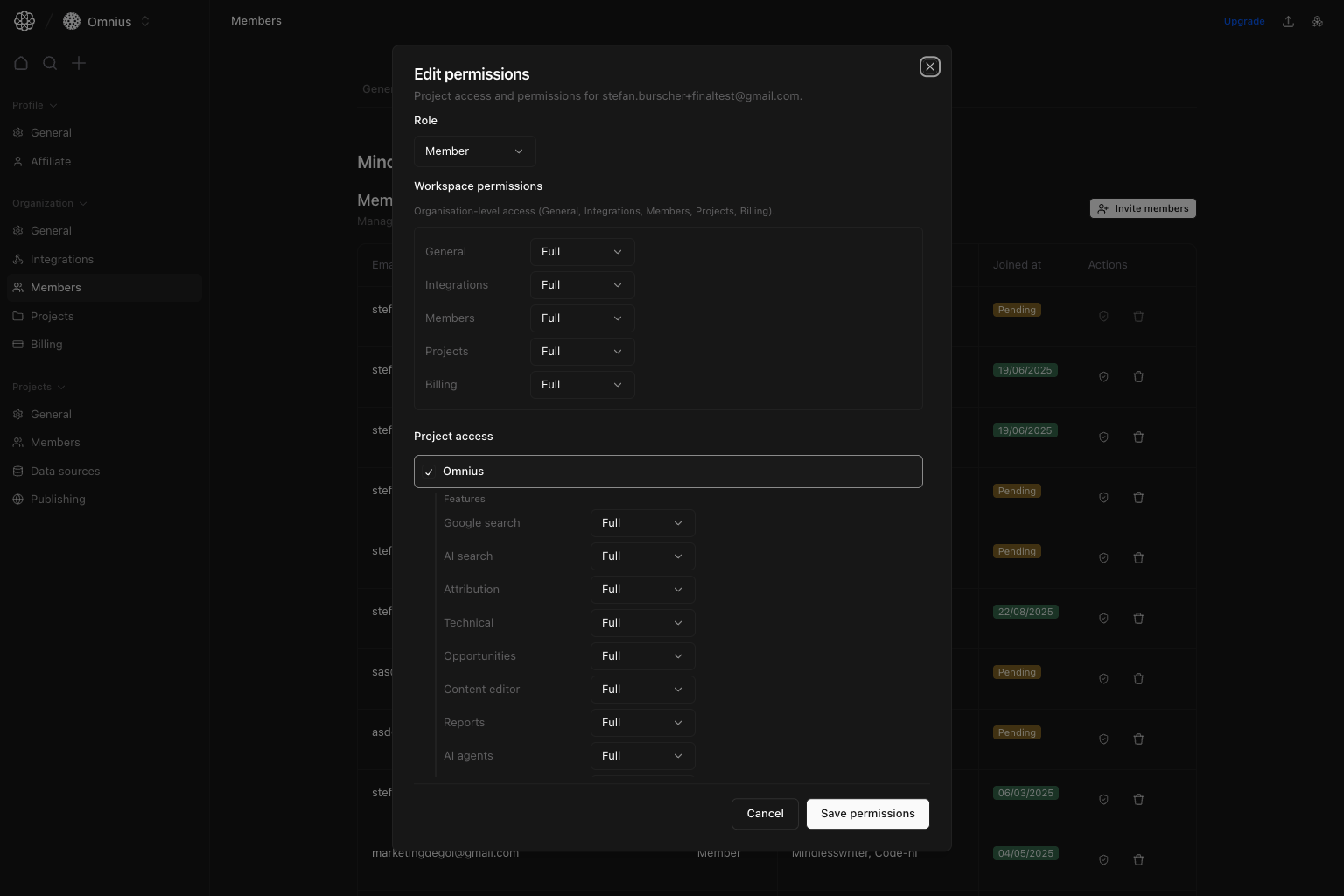
Edit permissions for an existing member.
What you can edit
- Role (
AdminorMember). - Workspace permission scopes.
- Project access selection.
- Per-project feature + settings permission scopes.
Permission scopes explained
The same 3 states are used across workspace and project permission rows:| Scope | What it means | Typical use case |
|---|---|---|
None | Feature is hidden/inaccessible for that member in that scope | Restrict access entirely |
View only | Member can see/read but cannot perform write actions (create/edit/delete/run) | Analyst/reviewer access without write rights |
Full | Member can view and perform write actions | Owner/operator who executes work |
Workspace-level permissions
These control access to organization settings sections:General:/settings/organization/generalIntegrations:/settings/organization/integrationsMembers:/settings/organization/membersProjects:/settings/organization/projectsBilling:/settings/organization/billing
Project feature permissions
These control feature access inside selected projects.| Permission key | UI label | Docs link |
|---|---|---|
GOOGLE_SEARCH | Google search | /data/google-search/overview |
AI_SEARCH | AI search | /data/ai-search/overview |
ATTRIBUTION | Attribution | /data/attribution/overview |
TECHNICAL | Technical | /data/technical/overview |
CONTENT_ANALYSIS | Opportunities | /data/opportunities/overview |
CONTENT_EDITOR | Content editor | /settings/project/brand-kit |
CUSTOM_REPORTS | Reports | /data/reports/overview |
AI_AGENTS | AI agents | /automation/agents/overview |
WORKFLOWS | Workflows | /automation/workflows/overview |
AUTOMATIONS | Automations | /automation/schedule/overview |
BRAND_KIT | Knowledge | /settings/project/brand-kit |
Project settings permissions
These control access to project settings tabs:| Permission key | UI label | Docs link |
|---|---|---|
SETTINGS_GENERAL | General | /settings/project/general |
SETTINGS_MEMBERS | Members | /settings/project/members |
SETTINGS_DATA_SOURCES | Data sources | /settings/project/data-sources |
SETTINGS_PUBLISHING | Publishing | /settings/project/publishing |
Practical permission patterns
- Client reviewer:
View onlyon reporting features,Noneon members/billing, limited project scope. - SEO operator:
Fullon data/technical/workflows in assigned projects,Noneon billing. - Organization admin:
Adminrole when they need global control.
Quick weekly checklist
- Resolve stale pending invites.
- Audit members with broad
Fullscopes. - Remove access for users no longer on account.
- Re-check project assignment breadth for each member.
Keep in mind
- Organization members can have different scopes per project.
- Role and permission scopes interact:
Adminbypasses granular restrictions. - Seat limits can block new invites until capacity is increased.

